How To Clean A Website That Was Infected With A Malware Virus?
Your website has been compromised, and you suspect the attackers accept injected malware into its lawmaking. What can you do almost it? There are many ways to approach a malware infection, and we'll wait at some in a moment, but your final recourse may exist to roll up your sleeves, hunt through the site's files, and remove the malware manually.
This article will testify y'all how to find malware lawmaking in your site's files and remove information technology, using a WordPress site as an example. Y'all don't have to be a developer to follow along, but you'll be better able to identify malware if you take some familiarity with coding and the linguistic communication the site is written in; PHP in WordPress's case.
How To Avoid Manually Removing Malware from Websites
In an platonic world, you wouldn't have to remove malware manually. It can be a tiresome process, especially if you lot tin can't distinguish betwixt malware and innocent code your site relies on. Information technology's as well piece of cake to miss malware code—online criminals are sneaky, and they go to dandy lengths to hide it. Unfortunately, you might spend hours hunting down and deleting malware traces, only for a subconscious backdoor to reinfect the site immediately.
The best choice is to avert malware infection in the first place. Make sure your site is updated, and turn on automatic updates if possible. Be conscientious when installing plugins and themes, and avoid nulled or pirate software at all costs; it is invariably loaded with malicious lawmaking.
Automatic malware detection and removal is also less enervating than manual malware removal. cPanel & WHM supports the excellent gratuitous ImmunifyAV scanner, which y'all can install via WHM's Security Center. It alerts yous when it finds a suspected malware infection and tells you lot where it is. If you upgrade to ImunifyAV+, you'll be able to remove malware with the click of a button likewise.
Finally, if y'all suspect an infection, you should attempt to restore a recent clean fill-in. Restoring from an uninfected backup overwrites malicious files with clean originals. cPanel'southward WordPress Toolkit makes it easy to support WordPress sites in seconds, or yous could use one of the many WordPress plugins that offer backup functionality.
If you don't have a recent fill-in, then you'll have to dig in and replace infected files manually.
Manually Removing Malware from a WordPress Site
Nosotros're using WordPress in our walkthrough because information technology'due south the near pop CMS, but a like process works just as well on other content management systems and ecommerce stores.
It should be mentioned that we're making a big assumption in this article. Nosotros're hoping the malicious lawmaking is limited to your website and that the attacker hasn't gained access to your spider web hosting server. However, if the server is compromised, the attacker may have replaced arrangement binaries with rootkits and other malware. If that's happened, you can't trust whatever software on the server, including the software we're about to use to clean malicious lawmaking from the site.
Earlier tackling malware removal on WordPress, yous should:
- Take the site offline. If possible, use WordPress Toolkit's maintenance mode to avoid exposing users to further risk.
- Make a backup. Back up your site whenever you make changes to its lawmaking or database.
- Plough on debug settings. Debug settings let WordPress to print mistake messages to the screen. They'll help you to figure out what went incorrect if you make changes that break the site. You can read more about debug settings and maintenance mode in WordPress® Debugging with cPanel and WordPress Toolkit.
First, nosotros'll check to see if any files have been modified in the last few days. About WordPress files are not oftentimes modified except for static avails like images, so recent changes are a helpful clue.
Log in to your server via SSH or open the cPanel Terminal and navigate to the infected site'due south directory. You'll notice the Terminal nether Advanced in the cPanel main page carte. Your WordPress site is most likely in public_html or a directory inside public_html.
Run the post-obit command:
find . -proper noun '*.ph*' -mtime -7 This displays a list of all PHP files modified in the terminal seven days. WordPress has hundreds of files that might hibernate malware, but let'southward assume that wp-config.php is at the top of your list. Next, nosotros demand to await within to see if there is whatever sign of malicious lawmaking.
Open the file in your text editor. If you lot prefer non to work with command-line text editors, locate the file in cPanel'due south File Managing director, and click Edit in the menu bar. You're looking for anything that seems out of place.
Keep an eye out for these red flags:
- Mismatched coding styles — the lines of code may be longer, improperly indented, or excessively complex.
- Obfuscated code — code that has been deliberately disguised. It looks like long strings of meaningless letters and numbers. Not all lawmaking that looks like this is malicious; you lot may come up beyond legitimate hashes that match this description, especially in configuration files.
- Strange URLs — virtually URLs in your site's files are related to the site itself. If you see an unusually formatted or excessively long spider web accost, information technology may link to a server under the aggressor's control.
For example, if yous see something like this mixed in with the familiar PHP code, information technology's almost certainly malware.
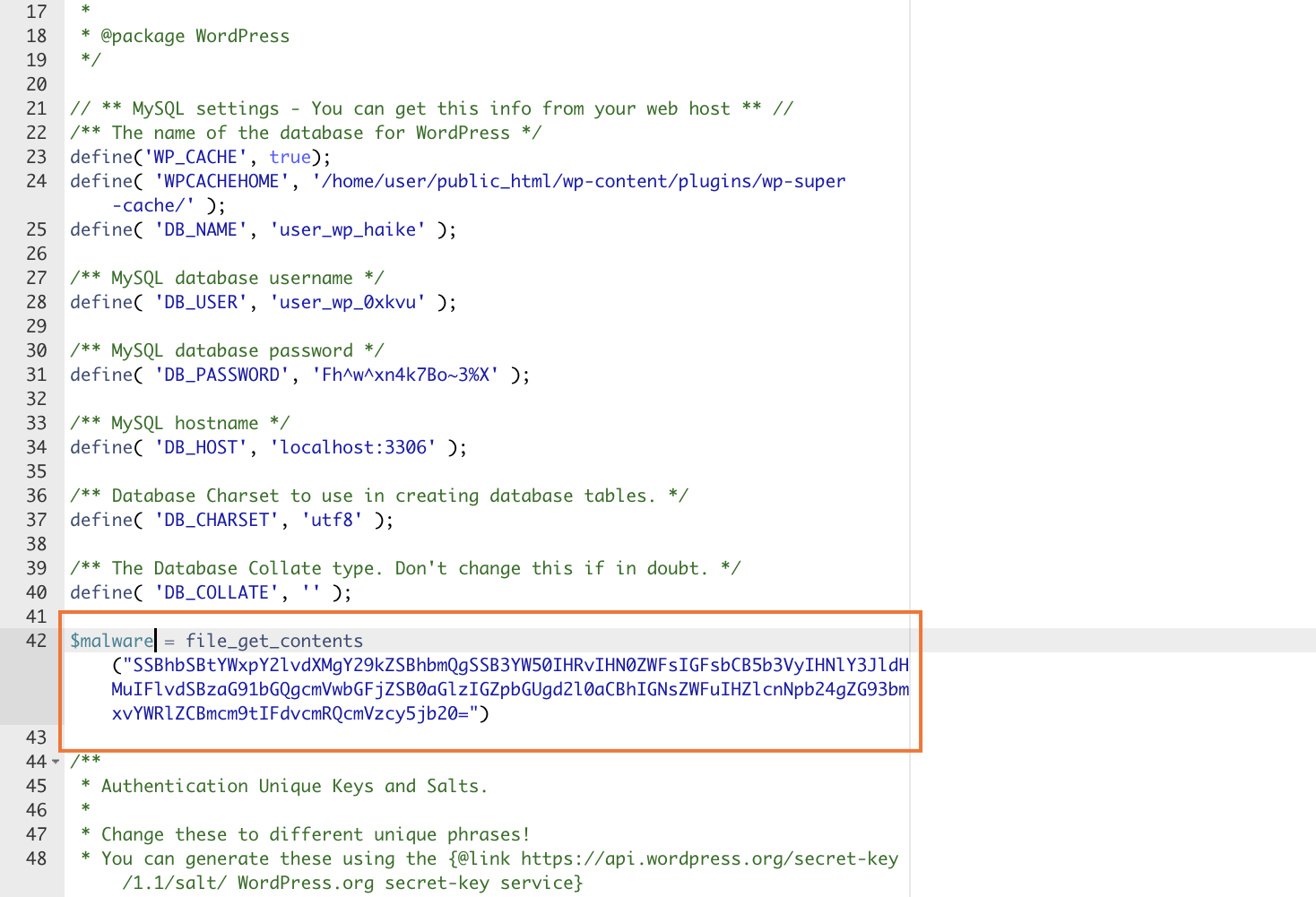
Most malicious lawmaking isn't that obvious. However, y'all can compare files with the original to run into if annihilation looks out of place. Download a fresh copy of the same version of WordPress from WordPress.org. If a plugin or theme file is under suspicion, download a new version from the programmer's site or the WordPress repository.
Open your newly downloaded version and compare it to your site's file. They may not be identical, merely yous should view whatever meaning differences with suspicion.
In many cases, y'all can only replace an infected file. Manually clearing malware is a careful procedure of exchanging infected files for uninfected originals. All the same, you must be careful not to just supplant files that contain essential configuration data. For example, if yous bandy wp-config.php for a freshly downloaded file, your site will stop working because that file contains site and database configurations.
If you aren't certain what a file does, cheque the WordPress documentation to ensure that information technology is safe to commutation. You lot may take to copy data from the infected file to its replacement, making sure no malicious lawmaking makes its way across.
To replace files, utilize cPanel'due south File Director to delete the infected original and upload the replacement. Then, verify the site still works every time you lot make a modify. If you don't regularly check and only discover the problem later, you may have no idea which edit did the damage.
Equally we mentioned at the get-go of this article, manual malware removal is a long and tedious process. And there is no guarantee that y'all'll find all the malicious lawmaking. However, it's a valuable technique to take nether your belt when automatic malware removal and back-ups let you down. As e'er, if y'all take whatsoever feedback or comments, delight let u.s. know. Nosotros are here to aid in the best ways we can. Y'all'll discover us on Discord, the cPanel forums, and Reddit. Be certain to likewise follow us on Facebook, Instagram, and Twitter.
Source: https://blog.cpanel.com/how-to-manually-remove-malware-from-websites/
Posted by: lewellenforneved.blogspot.com


0 Response to "How To Clean A Website That Was Infected With A Malware Virus?"
Post a Comment